The cybersecurity mesh market is experiencing significant growth as organizations worldwide prioritize safeguarding their digital assets against evolving cyber threats. A cybersecurity mesh refers to a decentralized, cloud-delivered security architecture that aims to provide scalable, flexible, and adaptive protection across various digital environments. This innovative approach moves away from the traditional perimeter-based security model, instead focusing on securing individual assets, devices, and identities wherever they reside within a network. With the proliferation of cloud computing, IoT devices, and remote work, the need for a more resilient and dynamic cybersecurity solution has become paramount, driving the adoption of cybersecurity mesh architectures.
Get a Sample: https://www.precedenceresearch.com/sample/3772
Growth Factors
Several factors contribute to the growth of the cybersecurity mesh market. Firstly, the increasing complexity and sophistication of cyber threats, including ransomware, phishing attacks, and zero-day exploits, are compelling organizations to adopt more robust security measures. Additionally, the rapid digitization of business processes and the proliferation of connected devices are expanding the attack surface, necessitating a more comprehensive security approach. Moreover, the rise of remote work and cloud adoption has blurred traditional network boundaries, creating a need for distributed security solutions like cybersecurity mesh to protect dispersed assets effectively.
Cybersecurity Mesh Market Scope
| Report Coverage | Details |
| Growth Rate from 2024 to 2033 | CAGR of 11% |
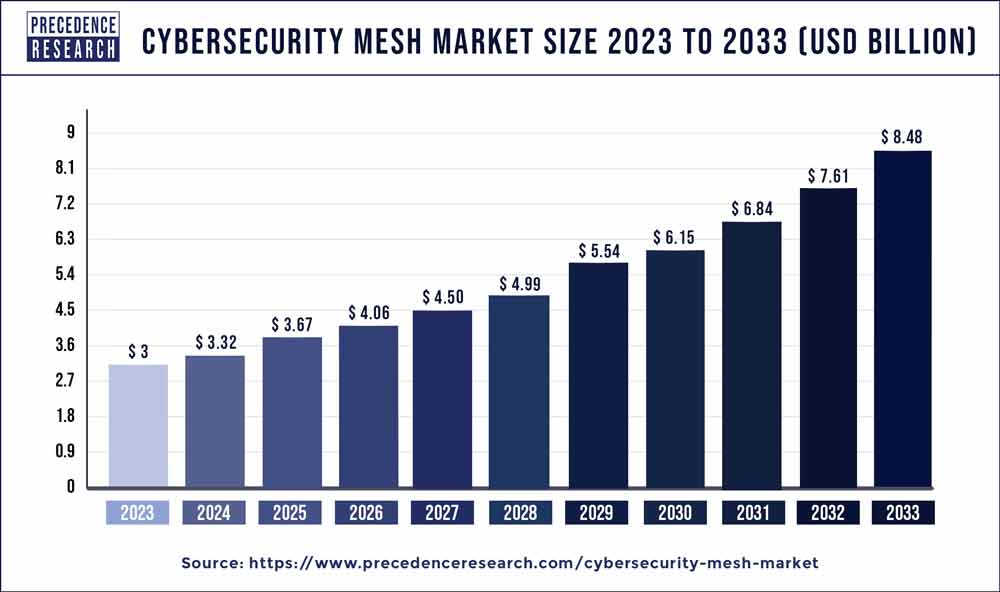
| Global Market Size in 2023 | USD 3 Billion |
| Global Market Size by 2033 | USD 8.48 Billion |
| U.S. Market Size in 2023 | USD 0.75 Billion |
| U.S. Market Size by 2033 | USD 2.16 Billion |
| Base Year | 2023 |
| Forecast Period | 2024 to 2033 |
| Segments Covered | By Offering, By Deployment, By Enterprise Size, and By Vertical |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Cybersecurity Mesh Market Dynamics
Drivers
Key drivers propelling the cybersecurity mesh market include the growing awareness of cybersecurity risks among businesses and the regulatory pressure to ensure data privacy and compliance. Furthermore, the shift towards hybrid and multi-cloud environments is driving demand for security solutions that can seamlessly integrate across diverse platforms. Additionally, the emergence of edge computing and 5G technology is fueling the demand for cybersecurity mesh solutions to secure edge devices and IoT ecosystems. Moreover, the increasing adoption of AI and machine learning for threat detection and response is enhancing the efficacy of cybersecurity mesh architectures, driving their adoption across various industries.
Restraints
Despite the promising growth prospects, the cybersecurity mesh market faces certain restraints. One of the primary challenges is the complexity of implementing and managing decentralized security architectures, particularly for organizations with legacy infrastructure and limited cybersecurity expertise. Additionally, concerns regarding interoperability and compatibility with existing security tools and platforms may hinder the adoption of cybersecurity mesh solutions. Moreover, the cost associated with deploying and maintaining comprehensive cybersecurity mesh environments could be prohibitive for some organizations, particularly smaller enterprises with budget constraints.
Opportunities
Despite the challenges, the cybersecurity mesh market presents significant opportunities for vendors and service providers. As organizations continue to invest in digital transformation initiatives, there is a growing demand for scalable and adaptive security solutions that can evolve with changing threat landscapes. Moreover, the increasing focus on zero-trust security models and identity-centric approaches presents an opportunity for cybersecurity mesh vendors to enhance their offerings with advanced authentication and access control capabilities. Additionally, partnerships and collaborations between cybersecurity vendors and cloud providers can accelerate the adoption of cybersecurity mesh solutions by offering integrated security services tailored to specific cloud environments. Furthermore, the rise of cybersecurity-as-a-service (CaaS) models presents an opportunity for organizations to outsource their security needs to specialized providers, driving the adoption of cybersecurity mesh architectures as a service offering.
Read Also: U.S. Digital Health Market Size will be USD 230.31 Bn by 2033
Recent Developments
- In October 2022, Check Point unveiled the Check Point Quantum Titan, a new release within the Check Point Quantum cybersecurity platform. The Quantum Titan release introduces three new software blades that harness AI and deep learning for advanced threat prevention against DNS, phishing, and autonomous IoT security. It provides IoT device discovery and automatically applies zero-trust threat prevention profiles to safeguard IoT devices.
- In September 2022, Zscaler completed the acquisition of ShiftRight, a leading provider of closed-loop security workflow automation technology. This technology is currently being integrated into the Zscaler Zero Trust Exchange cloud security platform, aiming to automate security management in response to the growing influx of risks and incidents that organizations face. The integration is designed to offer a simple yet sophisticated solution, significantly reducing incident resolution time.
- In May 2022, Lookout, a leader in endpoint-to-cloud security, and Ivanti announced a collaboration to assist organizations in accelerating cloud adoption and maturing their zero-trust security posture in the evolving workplace landscape. The integration of Ivanti Neurons for Zero Trust Access, Lookout CASB, and Lookout SWG aims to provide comprehensive threat prevention and data security both on-premises and in the cloud, both inside and outside the network, while adhering to zero-trust access security principles.
Cybersecurity Mesh Market Companies
To diversify their product offerings, companies in the industry employ various inorganic growth strategies, including forming partnerships, engaging in regular mergers, and pursuing acquisitions. A few of these prominent players are:
- IBM (US)
- Palo Alto Networks (US)
- Check Point (Israel)
- Zscaler (US)
- Fortinet (US)
- GCA Technology (US)
- Forcepoint (US)
- SonicWall (US)
- Ivanti (US)
- Cato Networks (Israel)
- Aryaka Networks (US)
- SailPoint (US)
- appNovi (US)
- Appgate (US)
- Mesh Security (Israel)
- Primeter 81 (Israel)
- Naoris Protocol (Portugal)
- Exium (US)
Segments Covered in the Report
By Offering
By Deployment
By Enterprise Size
- Small And Medium-Sized Enterprises (SMEs)
- Large enterprises
By Vertical
- BFSI
- Healthcare
- Energy Utilities
- IT and Telecom
- Government
- Others
By Geography
- North America
- Europe
- Asia-Pacific
- Latin America
- Middle East and Africa
Contact Us:
Mr. Alex
Sales Manager
Call: +1 9197 992 333
Email: sales@precedenceresearch.com
Web: https://www.precedenceresearch.com
Blog: https://www.expresswebwire.com/
Blog: https://www.uswebwire.com/
Blog: https://www.dailytechbulletin.com/
Blog: https://www.autoindustrybulletin.com/