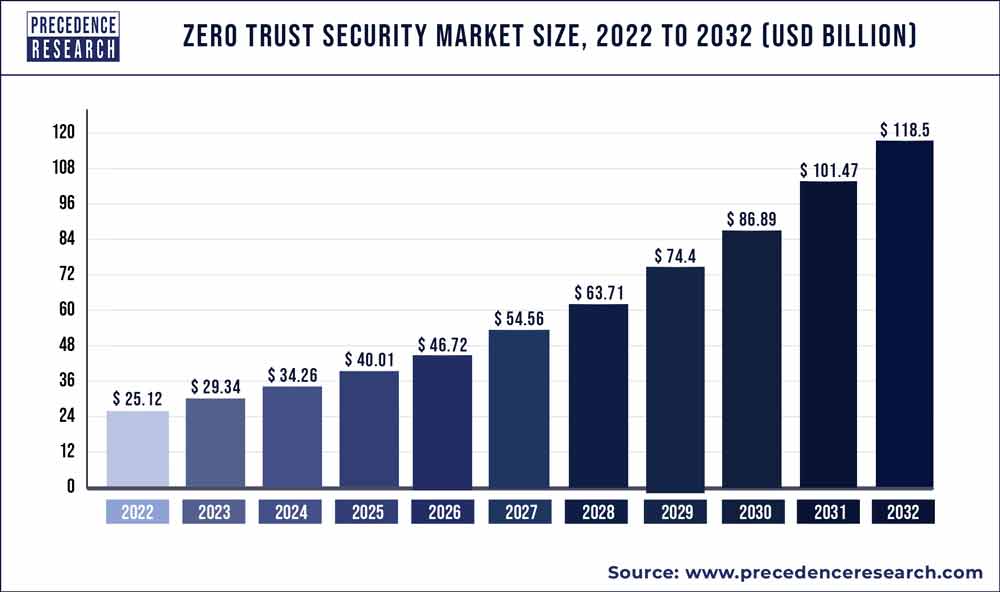
The global zero trust security market size accounted for US$ 25.12 Bn in 2022 and is projected to reach around USD 118.5 Bn by 2032, growing at a CAGR of 16.78% from 2023 to 2032.
Report Summary
The global zero trust security market report provides a Point-by-Point and In-Depth analysis of global market size, regional and country-level market size, market share, segmentation market growth, competitive landscape, sales analysis, opportunities analysis, strategic market growth analysis, the impact of domestic and global market key players, value chain optimization, trade regulations, recent developments, product launches, area marketplace expanding, and technological innovations.
The study offers a comprehensive analysis on diverse features, including production capacities, demand, product developments, revenue generation, and sales in the zero trust security market across the globe.
A comprehensive estimate on the zero trust security market has been provided through an optimistic scenario as well as a conservative scenario, taking into account the sales of zero trust security during the forecast period. Price point comparison by region with global average price is also considered in the study.
Download Access to a Free Copy of Our Latest Sample Report@ https://www.precedenceresearch.com/sample/3170
Zero Trust Security Market Report Scope
| Report Coverage | Details |
| Market Size in 2023 | USD 29.34 Billion |
| Market Size by 2032 | USD 118.5 Billion |
| Growth Rate from 2023 to 2032 | CAGR of 16.78% |
| Largest Market | North America |
| Base Year | 2022 |
| Forecast Period | 2023 To 2032 |
| Segments Covered | By Authentication Types, By Solution Type, and By Deployment Type |
| Regions Covered | North America, Europe, Asia-Pacific, Latin America, and Middle East & Africa |
Key Highlights:
Reports Coverage: It incorporates key market sections, key makers secured, the extent of items offered in the years considered, worldwide containerized zero trust security market and study goals. Moreover, it contacts the division study gave in the report based on the sort of item and applications.
Market Outline: This area stresses the key investigations, market development rate, serious scene, market drivers, patterns, and issues notwithstanding the naturally visible pointers.
Market Production by Region: The report conveys information identified with import and fare, income, creation, and key players of every single local market contemplated are canvassed right now.
Also Read: Cardiovascular Digital Solutions Market Size To Cross USD 183.23 Bn By 2032
Zero Trust Security Market Players
The report includes the profiles of key zero trust security market companies along with their SWOT analysis and market strategies. In addition, the report focuses on leading industry players with information such as company profiles, components and services offered, financial information, key development in past five years.
Major companies operating in this area
- Cisco Systems, Inc.
- Palo Alto Networks, Inc.
- Microsoft Corporation
- Symantec Corporation (now part of Broadcom Inc.)
- Okta, Inc.
- IBM Corporation
- Check Point Software Technologies Ltd.
- Akamai Technologies, Inc.
- Fortinet, Inc.
- CyberArk Software Ltd.
Market Segmentation
By Authentication Types
- Single-factor Authentication
- Multi-factor Authentication
By Solution Type
- Network Security
- Data Security
- Endpoint Security
- API Security
- Cloud Security
- Others
By Deployment Type
- Cloud
- On-Premises
Regional Segmentation
- North America (U.S., Canada, Mexico)
- Europe (Germany, France, U.K., Italy, Spain, Rest of Europe)
- Asia-Pacific (China, Japan, India, Southeast Asia and Rest of APAC)
- Latin America (Brazil and Rest of Latin America)
- Middle East and Africa (GCC, North Africa, South Africa, Rest of MEA)
Research Methodology
Secondary Research
It involves company databases such as Hoover’s: This assists us to recognize financial information, the structure of the market participants and industry’s competitive landscape.
The secondary research sources referred in the process are as follows:
- Governmental bodies, and organizations creating economic policies
- National and international social welfare institutions
- Company websites, financial reports and SEC filings, broker and investor reports
- Related patent and regulatory databases
- Statistical databases and market reports
- Corporate Presentations, news, press release, and specification sheet of Manufacturers
Primary Research
Primary research includes face-to-face interviews, online surveys, and telephonic interviews.
- Means of primary research: Email interactions, telephonic discussions and Questionnaire-based research etc.
- In order to validate our research findings and analysis, we conduct primary interviews of key industry participants. Insights from primary respondents help in validating the secondary research findings. It also develops Research Team’s expertise and market understanding.
TABLE OF CONTENT
Chapter 1. Introduction
1.1. Research Objective
1.2. Scope of the Study
1.3. Definition
Chapter 2. Research Methodology (Premium Insights)
2.1. Research Approach
2.2. Data Sources
2.3. Assumptions & Limitations
Chapter 3. Executive Summary
3.1. Market Snapshot
Chapter 4. Market Variables and Scope
4.1. Introduction
4.2. Market Classification and Scope
4.3. Industry Value Chain Analysis
4.3.1. Raw Material Procurement Analysis
4.3.2. Sales and Distribution Channel Analysis
4.3.3. Downstream Buyer Analysis
Chapter 5. COVID 19 Impact on Zero Trust Security Market
5.1. COVID-19 Landscape: Zero Trust Security Industry Impact
5.2. COVID 19 – Impact Assessment for the Industry
5.3. COVID 19 Impact: Global Major Government Policy
5.4. Market Trends and Opportunities in the COVID-19 Landscape
Chapter 6. Market Dynamics Analysis and Trends
6.1. Market Dynamics
6.1.1. Market Drivers
6.1.2. Market Restraints
6.1.3. Market Opportunities
6.2. Porter’s Five Forces Analysis
6.2.1. Bargaining power of suppliers
6.2.2. Bargaining power of buyers
6.2.3. Threat of substitute
6.2.4. Threat of new entrants
6.2.5. Degree of competition
Chapter 7. Competitive Landscape
7.1.1. Company Market Share/Positioning Analysis
7.1.2. Key Strategies Adopted by Players
7.1.3. Vendor Landscape
7.1.3.1. List of Suppliers
7.1.3.2. List of Buyers
Chapter 8. Global Zero Trust Security Market, By Authentication Types
8.1. Zero Trust Security Market, by Authentication Types, 2023-2032
8.1.1 Single-factor Authentication
8.1.1.1. Market Revenue and Forecast (2020-2032)
8.1.2. Multi-factor Authentication
8.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 9. Global Zero Trust Security Market, By Solution Type
9.1. Zero Trust Security Market, by Solution Type, 2023-2032
9.1.1. Network Security
9.1.1.1. Market Revenue and Forecast (2020-2032)
9.1.2. Data Security
9.1.2.1. Market Revenue and Forecast (2020-2032)
9.1.3. Endpoint Security
9.1.3.1. Market Revenue and Forecast (2020-2032)
9.1.4. API Security
9.1.4.1. Market Revenue and Forecast (2020-2032)
9.1.5. Cloud Security
9.1.5.1. Market Revenue and Forecast (2020-2032)
9.1.6. Others
9.1.6.1. Market Revenue and Forecast (2020-2032)
Chapter 10. Global Zero Trust Security Market, By Deployment Type
10.1. Zero Trust Security Market, by Deployment Type, 2023-2032
10.1.1. Cloud
10.1.1.1. Market Revenue and Forecast (2020-2032)
10.1.2. On-Premises
10.1.2.1. Market Revenue and Forecast (2020-2032)
Chapter 11. Global Zero Trust Security Market, Regional Estimates and Trend Forecast
11.1. North America
11.1.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.4. U.S.
11.1.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.1.5. Rest of North America
11.1.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.1.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.1.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2. Europe
11.2.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.4. UK
11.2.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.5. Germany
11.2.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.6. France
11.2.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.2.7. Rest of Europe
11.2.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.2.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.2.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3. APAC
11.3.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.4. India
11.3.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.5. China
11.3.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.6. Japan
11.3.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.3.7. Rest of APAC
11.3.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.3.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.3.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4. MEA
11.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.4. GCC
11.4.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.5. North Africa
11.4.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.6. South Africa
11.4.6.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.6.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.6.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.4.7. Rest of MEA
11.4.7.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.4.7.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.4.7.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5. Latin America
11.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.4. Brazil
11.5.4.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.4.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.4.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
11.5.5. Rest of LATAM
11.5.5.1. Market Revenue and Forecast, by Authentication Types (2020-2032)
11.5.5.2. Market Revenue and Forecast, by Solution Type (2020-2032)
11.5.5.3. Market Revenue and Forecast, by Deployment Type (2020-2032)
Chapter 12. Company Profiles
12.1. Cisco Systems, Inc.
12.1.1. Company Overview
12.1.2. Product Offerings
12.1.3. Financial Performance
12.1.4. Recent Initiatives
12.2. Palo Alto Networks, Inc.
12.2.1. Company Overview
12.2.2. Product Offerings
12.2.3. Financial Performance
12.2.4. Recent Initiatives
12.3. Microsoft Corporation
12.3.1. Company Overview
12.3.2. Product Offerings
12.3.3. Financial Performance
12.3.4. Recent Initiatives
12.4. Symantec Corporation (now part of Broadcom Inc.)
12.4.1. Company Overview
12.4.2. Product Offerings
12.4.3. Financial Performance
12.4.4. Recent Initiatives
12.5. Okta, Inc.
12.5.1. Company Overview
12.5.2. Product Offerings
12.5.3. Financial Performance
12.5.4. Recent Initiatives
12.6. IBM Corporation
12.6.1. Company Overview
12.6.2. Product Offerings
12.6.3. Financial Performance
12.6.4. Recent Initiatives
12.7. Check Point Software Technologies Ltd.
12.7.1. Company Overview
12.7.2. Product Offerings
12.7.3. Financial Performance
12.7.4. Recent Initiatives
12.8. Akamai Technologies, Inc.
12.8.1. Company Overview
12.8.2. Product Offerings
12.8.3. Financial Performance
12.8.4. Recent Initiatives
12.9. Fortinet, Inc.
12.9.1. Company Overview
12.9.2. Product Offerings
12.9.3. Financial Performance
12.9.4. Recent Initiatives
12.10. CyberArk Software Ltd.
12.10.1. Company Overview
12.10.2. Product Offerings
12.10.3. Financial Performance
12.10.4. Recent Initiatives
Chapter 13. Research Methodology
13.1. Primary Research
13.2. Secondary Research
13.3. Assumptions
Chapter 14. Appendix
14.1. About Us
14.2. Glossary of Terms
Thanks for reading you can also get individual chapter-wise sections or region-wise report versions such as North America, Europe, or the Asia Pacific.
Contact Us:
Mr. Alex
Sales Manager
Call: +1 9197 992 333
Email: sales@precedenceresearch.com
